Course Design By
Nasscom & Wipro
Teachers in Cyber Security Online Course will assist you in developing your communication by engaging you in various discussions, and interactions related to the topic.
You will have access to the LMS portal, where you can see class teachings, assignments, etc.
After joining Cyber Security Online Training in India, you will be provided with sufficient study material as well.
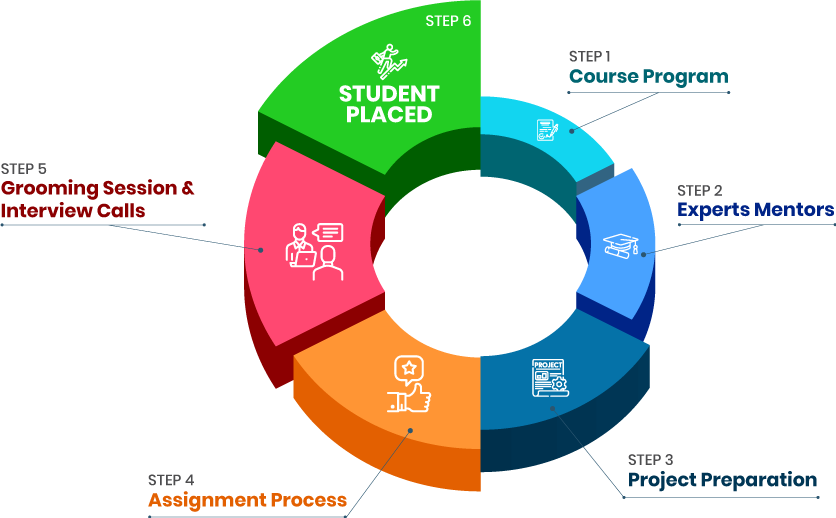
After completing the Cyber Security Online Course, instructors will take you through the placement process.
Training in network security and network protocol to protect from threats.
Learn penetration testing in system security assessment.
Be introduced to cloud security and virtual environment protection.
Risk Management
Threat Intelligence
Vulnerability Management
Security Operations
Incident Response
Access Control
Network Security
Cryptography
Compliance and Governance
Security Architecture and Design
Security Auditing
Endpoint Security
Application Security
Data Security
Cloud Security
Wireshark
Nmap
Metasploit
Kali Linux
Burp Suite
Nessus
OpenVAS
Maltego
Snort
Aircrack-ng
John the Ripper
OSSEC
Splunk
Nikto
Hydra
ZAP (Zed Attack Proxy)
Hashcat
Fail2Ban
Tcpdump
Tripwire
Issuer: (ISC)
Master-level certification on overall security topic areas such as asset security, risk management, etc.
Issuer: EC-Council
Start with an offensive security focus and teach penetration testing for vulnerability identification from the hacker's point of view.
Issued by: ISACA
Security management and governance focus starting point, best for risk managers, incident response managers.
Issued by: ISACA
Governance and security audit focus starting point, best for information systems monitoring specialists.
Issued by: (ISC)
Cloud risk management and cloud security expert best placed to protect cloud infrastructure.
Issuer: CompTIA
lower-level foundation certificate with network security and cryptography emphasis.
Issuer: EC-Council
Penetration testing certified to mimic cyber-attacks to identify vulnerabilities.
Issuer: EC-Council
Network defenders like monitoring and risk mitigation processes.
Issuer: GIAC
Network security, cryptography, and risk management foundation certification.
Issuer: CompTIA
Mid-level certification for threat response and detection professionals.
Issuer: EC-Council
Security Operations Center (SOC) activity awareness, e.g., incident response and detection.
Issuer: ISACA
Suitable for IT risk management professionals in a professional career for governance.
Issuer: Microsoft
Competence in security of the Microsoft Azure platform, identity, and threat defense.
Issuer: Amazon Web Services (AWS)
It encompasses AWS cloud infrastructure security, data encryption, and incident response.
Issuer: CNCF
Hands-on experience in Kubernetes and containerized environment security is best suited for DevOps engineers.
Cyber Security Analyst: $50,000 to $70,000 annually.
Network Security Engineer: $55,000 to $75,000 annually.
Penetration Tester: $60,000 - $80,000 per annum.
IT Security Administrator: $55,000 - $70,000 per annum.
Junior Analyst to Senior Security Analyst in 2-4 years
Professionals get expert positions such as Penetration Tester, Ethical Hacker, or Forensic Analyst.
Growth into management positions such as Cybersecurity Manager, Security Consultant, or Chief Information Security Officer (CISO).
Certification through continuing education, e.g., CISSP, CEH, and CompTIA Security+, will support career development.
AI-driven security will be unavoidable in 2025 to identify and automate threats.
Zero-Trust would be the default, where there is ongoing verification of users and devices.
Cloud security would give way to multi-cloud security, and the IoT devices spree would call for more stringent security.
Growing compliance requirements,
Accelerating cloud computing adoption
IoT, and AI, and the emerging risks of cyberattacks from them.
Cyber Security Analyst: Secure networks free from security breaches, perform risk analysis, and put security measures into action.
Penetration Tester (Ethical Hacker): Simulate test attacks on systems to identify vulnerabilities and suggest solutions.
Security Consultant: Guide organizations on best practices for streamlining their security infrastructure.
Incident Response Analyst: Coordinate and manage security breaches and incidents.
Security Architect: Design, develop, and deploy security infrastructure for organizations.
Government
Healthcare
Tech
Telecommunications
we train you to get hired.
By registering here, I agree to Croma Campus Terms & Conditions and Privacy Policy
+ More Lessons
Course Design By
Nasscom & Wipro
Course Offered By
Croma Campus
Stories
success
inspiration
career upgrade
career upgrade
career upgrade
career upgrade
You will get certificate after
completion of program
You will get certificate after
completion of program
You will get certificate after
completion of program
in Collaboration with

Empowering Learning Through Real Experiences and Innovation
we train you to get hired.
Phone (For Voice Call):
+91-971 152 6942WhatsApp (For Call & Chat):
+91-971 152 6942Get a peek through the entire curriculum designed that ensures Placement Guidance
Course Design By
Course Offered By
Ready to streamline Your Process? Submit Your batch request today!
All the studies are concluded within 6 months to 1 year, part-time or full-time.
Some basic knowledge in IT is always welcome, but not required. The course is to be taught right from scratch.
Yes, our placement department assists students with internship and job placements upon course completion.
You become certified by industry professionals, and certifications such as CEH, CompTIA, and CISSP would also be offered.
Yes, we also offer courses online for those students who cannot attend class physically.

Highest Salary Offered
Average Salary Hike
Placed in MNC’s
Year’s in Training

fast-tracked into managerial careers.
Get inspired by their progress in the
Career Growth Report.
FOR QUERIES, FEEDBACK OR ASSISTANCE
Best of support with us
For Voice Call
+91-971 152 6942For Whatsapp Call & Chat
+91-9711526942