Course Design By
Nasscom & Wipro
You will have a deeper understanding of concepts, approaches, principles, and objectives.
You can analyze both functional and non-functional specifications.
You will learn how to use and select various testing tools with our Cyber Security Training Institute in Gurgaon.
Understand legal limits, privacy problems, and audit process techniques in the cloud context.
Focus on IT compliance and the integrity of enterprise systems to establish a more secure enterprise IT infrastructure.
To ensure security, set up and configure firewalls and intrusion detection systems.
Ensure that security-related devices and software are up to date.
Plan and monitor the network system as a whole.
Establish security policies.
Install security infrastructure devices to maintain the security of the VPC, web protocols, and email.
To detect malicious incidents, conduct security and forensic analyses.
we train you to get hired.

By registering here, I agree to Croma Campus Terms & Conditions and Privacy Policy
+ More Lessons
Course Design By

Nasscom & Wipro
Course Offered By

Croma Campus

Stories
success
inspiration


career upgrad

career upgrad


career upgrad


career upgrad
12-Jul-2025*
14-Jul-2025*
09-Jul-2025*
12-Jul-2025*
14-Jul-2025*
09-Jul-2025*

You will get certificate after
completion of program

You will get certificate after
completion of program

You will get certificate after
completion of program
in Collaboration with






Empowering Learning Through Real Experiences and Innovation
we train you to get hired.
Phone (For Voice Call):
+91-971 152 6942WhatsApp (For Call & Chat):
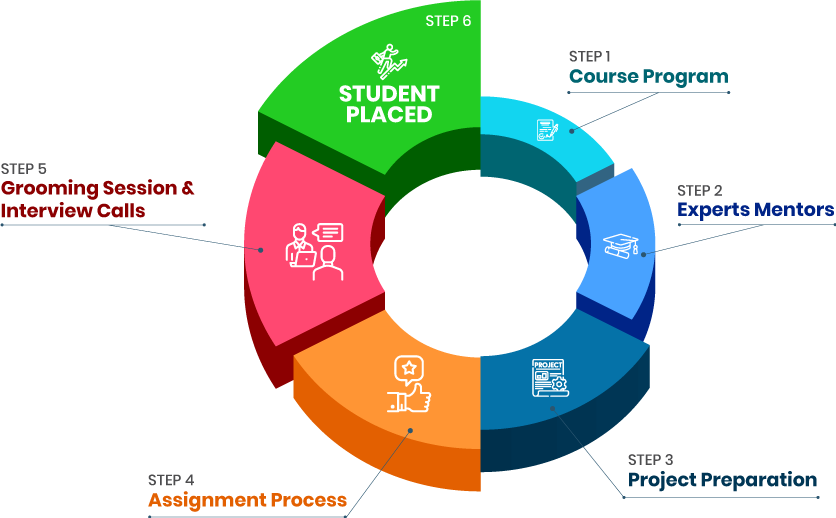
+91-971 152 6942Get a peek through the entire curriculum designed that ensures Placement Guidance
Course Design By


Course Offered By

Ready to streamline Your Process? Submit Your batch request today!
Cyber Security Training at Croma campus offers a unique vision into the world of hand-on practical Cyber Security Training. Croma campus is the Best Cyber Security Training Institute in Gurgaon. Because The adviser handling Cyber Security Training tips a trade experience of more than 10+ years. The view of becoming a freelancer growth harshly with the arsenal of Cyber Security Online in one’s portfolio. According to manifold reviews over the internet, we Ranked Best Cyber Security Training in Gurgaon.
Croma campus is the Legend in offering placement to the students. Please visit our Placed Students List on our website. More than 2000+ students placed last year. It has a dedicated placement portal that caters to the needs of the students during placements. Croma campus conducts development sessions, including mock interviews, presentation skills to prepare students to face a challenging interview situation with ease. 100% placement record. 1000+ interviews organized.
Your course conclusion certificate will be auto made in the LMS once you see the below criteria
This Project will put you in an online corporate location. You will be coding a demo lending website. You will create & run code and have an opening to associate it with easy code created by our experts in real-time. The plan will last 7 days. You will be sent 1 email every 24 hours with your work provision for that day. It is totally FREE.
The ways to connect Croma Campus.

FOR QUERIES, FEEDBACK OR ASSISTANCE
Best of support with us
For Voice Call
+91-971 152 6942For Whatsapp Call & Chat
+91-9711526942