Course Design By
Nasscom & Wipro
Here, at Croma Campus Cyber Security Online Training in India you will get the opportunity to acquire in-depth Cybersecurity online training in this course by our experienced faculty members.
In Cyber Security Online Course, our faculty members will help you to enhance your communication by indulging you in numerous discussions, and interactions concerning the subject.
You will get access to our LMS portal, where you will find class teachings, assignments, etc.
After enrolling in Cyber Security Online Training in India, you will be given enough study material also.
Post completing the Cyber Security Online Course, our trainers will put you through the placement process.
Furthermore, you will receive sessions regarding its enterprise architecture and elements.
Our team will also let you know the information system, governance, and risk assessment.
Moreover, you will be given a quite qualitative session regarding the incident management section as well.
Risk Management: This module teaches you how to identify, assess, and reduce risks that could harm an organizations assets and operations. You'll learn to develop strategies that not only minimize risks but also align with the companys overall goals. Risk management is significant for building resilience against unexpected challenges.
Threat Intelligence: In this module, you will explore how to gather and analyze data about potential threats. You'll learn to recognize and track cyber-attacks before they happen, giving you the upper hand in protecting your organization. Understanding threat intelligence is key to staying one step ahead of cybercriminals.
Vulnerability Management: Here, youll discover how to spot, classify, and address weaknesses in your IT systems. You will gain hands-on experience with tools for scanning and patching vulnerabilities, ensuring that potential threats are fixed before they can be exploited. A strong vulnerability management process is vital for maintaining security.
Security Operations: This module focuses on the daily tasks needed to keep systems secure from attacks. You will learn about monitoring security events and responding to threats in real-time. Effective security operations help ensure that your organization is always prepared for any potential breaches.
Incident Response: You will learn strategies for reacting effectively to security incidents in this module. By mastering the steps of detection, containment, and recovery, youll minimize damage and ensure quick recovery. A well-prepared incident response plan is essential for maintaining trust and stability in an organization.
Access Control: This module covers methods for ensuring that only authorized individuals can access sensitive systems and data. You will explore user authentication and identity management techniques. Proper access control not only protects your assets but also fosters a culture of accountability within the organization.
Network Security: In this module, youll discover how to safeguard networks against unauthorized access and attacks. You will learn about essential tools like firewalls and intrusion detection systems. A solid understanding of network security is crucial in today's interconnected world, where threats can emerge from anywhere.
Cryptography: You will explore the art of securing communication and protecting data through cryptography in this module. By learning about encryption techniques and key management, you'll understand how to keep sensitive information safe. Cryptography is like a digital lock that ensures only the right people can access valuable data.
Compliance and Governance: This module emphasizes aligning your security practices with legal and regulatory standards. Youll learn about important frameworks such as GDPR and HIPAA, ensuring your organization meets compliance requirements. Understanding compliance and governance is essential for building trust and credibility with stakeholders.
Security Architecture and Design: Here, you will dive into creating secure IT systems from the ground up. Youll learn about security layers and how to design infrastructures that are resilient to attacks. A well-thought-out security architecture is like a blueprint for protecting your organization's most valuable assets.
Security Auditing: This module teaches you how to conduct thorough audits to assess an organization's security measures. You will gain skills in identifying vulnerabilities and making recommendations for improvement. Regular security audits are key to ensuring that your organization stays compliant and secure over time.
Endpoint Security: You will learn how to protect devices like laptops and smartphones from cyber threats in this module. By exploring various security measures, you'll ensure that even mobile devices are secure. As remote work becomes more common, endpoint security is essential for keeping sensitive information safe.
Application Security: In this module, you will discover how to protect software applications from vulnerabilities. You will learn secure coding practices and how to test for security flaws. Application security is crucial because a single vulnerability can compromise an entire system, making this knowledge invaluable.
Data Security: This module focuses on keeping data safe from unauthorized access and theft. You'll learn techniques like encryption and secure storage to protect sensitive information. With the increasing importance of data privacy, understanding data security has never been more important for businesses.
Cloud Security: Here, you will learn how to secure cloud-based systems and services. Youll explore identity management, data encryption, and monitoring for potential threats. As more companies move to the cloud, understanding cloud security is important for protecting both data and business operations.
Wireshark: Wireshark is like a magnifying glass for your network. It captures and analyzes data flowing through your system, helping you spot anything unusual. Whether its troubleshooting or finding hidden threats, Wireshark lets cybersecurity professionals dig deep into network traffic.
Nmap: Nmap is your go-to for mapping out a network. It helps you discover devices, services, and open ports, which gives you a clear view of whats going on in your system. With Nmap, you can spot vulnerabilities before attackers do, making your network more secure.
Metasploit: Metasploit is the ultimate ethical hacking toolkit. It lets cybersecurity experts simulate attacks to test the strength of systems. You can find weak spots, run tests, and make sure your defenses are up to the task, all within a safe, controlled environment.
Kali Linux: Kali Linux is a hackers Swiss Army knife. Its packed with hundreds of cybersecurity tools, all geared toward penetration testing and security analysis. From scanning networks to cracking passwords, Kali Linux gives security pros everything they need to assess and strengthen systems.
Burp Suite: Burp Suite is the best friend of web security testers. It helps find vulnerabilities in web applications like SQL injections and cross-site scripting (XSS). With its automated and manual testing features, Burp Suite ensures your web apps are secure from hackers.
Nessus: Nessus scans your systems for potential weaknesses, like missing patches or outdated software. Think of it as a health check for your network, where doctor conducts a thorough medical examination to detect any underlying issues. It helps organizations detect vulnerabilities and provides reports on how to fix them, keeping systems safe from attack.
OpenVAS: OpenVAS is an open-source tool that continuously scans your network for vulnerabilities. It keeps an eye out for any potential threats, helping organizations identify and resolve issues before attackers can exploit them. Its like a security watchdog for your systems.
Maltego: Maltego helps you connect the dots in your cybersecurity investigations. It collects and visualizes data from different sources, showing relationships between domains, IPs, and more. Its perfect for threat intelligence and finding hidden connections in digital footprints.
Snort: Snort acts as a security guard for your network. It watches traffic in real time, alerting you to anything suspicious. Whether its detecting malware or preventing intrusions, Snort is essential for keeping networks safe from a wide range of cyber threats.
Aircrack-ng: Aircrack-ng is a toolset for testing the security of wireless networks. It helps cybersecurity experts crack Wi-Fi encryption keys to assess how secure the network really is. By finding weak points, you can prevent attackers from exploiting them.
John the Ripper: John the Ripper is a password-cracking tool that shows just how strong (or weak) your passwords are. It helps uncover weak credentials through brute-force or dictionary attacks, allowing organizations to improve password policies and ensure better protection.
OSSEC: OSSEC is like a guard dog for your system files. It constantly monitors activity, looking for any changes or threats. If anything suspicious happens, it sends alerts, helping organizations respond quickly to potential breaches and keep their systems secure.
Splunk: Splunk is a powerhouse for analyzing security data. It helps cybersecurity teams monitor logs, detect incidents, and investigate threats in real time. Splunk is used to search and analyze large amounts of machine-generated data, turning it into actionable insights.
Nikto: Nikto scans web servers for potential security risks. It checks for outdated software and misconfigurations that could lead to vulnerabilities. Cybersecurity professionals use Nikto to secure web servers and ensure that theyre not easy targets for attacks.
Hydra: Hydra is a tool for testing the strength of passwords and login credentials. Its great for uncovering weak points in authentication systems by trying various username and password combinations. This helps organizations reinforce their security and lock down access points.
ZAP (Zed Attack Proxy): ZAP is an open-source tool for finding security vulnerabilities in web applications. Its user-friendly, making it ideal for both beginners and pros to identify flaws like cross-site scripting and SQL injection, helping secure your web apps before attackers can exploit them.
Hashcat: Hashcat is a fast password-cracking tool that supports a wide range of hash types. It uses CPUs and GPUs to crack passwords at lightning speed, making it a powerful tool for cybersecurity experts to test the strength of passwords and hashes.
Fail2Ban: Fail2Ban helps protect servers from brute-force attacks. It monitors failed login attempts and bans IP addresses that repeatedly try to break in. By automatically blocking suspicious activity, Fail2Ban reduces the risk of unauthorized access to sensitive systems.
Tcpdump: Tcpdump is a tool for capturing and analyzing network traffic. It gives cybersecurity professionals detailed insights into whats happening on a network, allowing them to detect suspicious behavior, troubleshoot issues, and secure their systems against potential attacks.
Tripwire: Tripwire is all about keeping files and systems intact. It monitors critical files and alerts you if anything changes unexpectedly. Its perfect for organizations that need to maintain system integrity and detect any unauthorized changes to important data or configurations.
Network Security: Network security is all about keeping your data safe as it travels over networks. This involves using tools like firewalls and VPNs to create a secure environment. Mastering network security is crucial, as it lays the groundwork for protecting your entire organization against cyber threats.
Firewalls: Firewalls are like gatekeepers for your network, controlling what traffic can enter and exit. They analyze data packets based on set security rules. Understanding how to set up and manage firewalls is essential for ensuring your organization's data stays safe and sound from unauthorized access.
Intrusion Detection Systems (IDS): Intrusion Detection Systems are vigilant watchers for your network, constantly monitoring for suspicious activities. They alert you to potential threats, allowing for quick action. Learning to use IDS effectively is key for identifying risks before they can escalate into serious security incidents.
Intrusion Prevention Systems (IPS): IPS not only detects potential threats but also takes action to stop them in their tracks. By blocking malicious traffic, they serve as an active defense mechanism. Gaining expertise in IPS helps you bolster your security measures and protect your organization from evolving cyber threats.
Encryption: Encryption is like putting your sensitive data in a locked box that only authorized users can open. This ensures confidentiality and integrity during data storage and transmission. Mastering encryption techniques is vital for any cybersecurity professional looking to keep sensitive information safe from prying eyes.
Vulnerability Assessment: Vulnerability assessments are like health check-ups for your systems, identifying weaknesses that could be exploited by attackers. Conducting these assessments regularly helps organizations strengthen their defenses. This skill is essential for recognizing potential risks and improving overall cybersecurity.
Penetration Testing: Penetration testing simulates cyber-attacks to find vulnerabilities before malicious hackers can. By learning how to conduct these tests, you can proactively secure your systems and enhance your organization's defenses. Its an essential skill for staying one step ahead of cybercriminals.
Security Information and Event Management (SIEM): SIEM systems aggregate and analyze security data, helping you spot threats in real-time. By mastering SIEM tools, you can improve your incident response and maintain compliance. This knowledge is critical for keeping your organization secure and informed about potential risks.
Risk Management: Risk management involves identifying and prioritizing risks to mitigate their impact. This skill is vital for developing effective security strategies and ensuring resources are allocated efficiently. It helps organizations make informed decisions to protect their assets and reputation.
Security Policies and Procedures: Understanding security policies and procedures helps create a structured approach to data protection. This includes developing guidelines for handling sensitive information and incident response. By mastering this area, you can foster a culture of security awareness within your organization.
Endpoint Security: Endpoint security is all about protecting devices like laptops and smartphones from threats. With more people working remotely, this skill has become increasingly important. By implementing strong endpoint security measures, you can safeguard devices and sensitive data from potential breaches.
Access Control: Access control access will be granted to sensitive information and systems only to authorized users. This involves authentication and authorization techniques. Learning about access control is crucial for maintaining data security and preventing unauthorized access to critical resources.
Incident Response: Incident response is the process of preparing for and managing security breaches. Knowing how to effectively respond can minimize damage and ensure a swift recovery. This skill is essential for maintaining business continuity in an ever-evolving threat landscape.
Malware Analysis: Malware analysis helps you understand how malicious software operates. By learning to analyze malware, you can develop effective strategies to counteract its effects. This skill is key for protecting systems and minimizing the impact of cyber threats.
Threat Hunting: Threat hunting is the proactive search for hidden threats within your network. By mastering this skill, you can identify and neutralize risks before they can cause damage. Its an essential part of staying ahead in the cybersecurity game.
Forensics: Forensics involves investigating security incidents to uncover what happened and gather evidence. This skill is essential for understanding breaches and improving future defenses. Knowledge of forensic techniques can help organizations learn from their mistakes and strengthen security protocols.
Cloud Security: Cloud security focuses on the protection of data and applications stored in the cloud. With the increasing reliance on cloud services, this skill is critical for safeguarding information. By understanding cloud security best practices, you can help organizations securely navigate the cloud landscape.
Identity and Access Management (IAM): IAM involves managing user identities and controlling access to resources. This includes user provisioning and role-based access. Mastering IAM is crucial for ensuring that sensitive data is only accessible to those who truly need it, thus enhancing overall security.
Secure Software Development: Secure software development integrates security practices into the development process. By learning secure coding techniques, you can reduce vulnerabilities in applications from the start. This proactive approach is essential for developing resilient software that can withstand cyber threats.
Compliance and Regulatory Standards: Understanding compliance and regulatory standards is vital for ensuring organizations meet legal and industry requirements. This knowledge helps you implement effective security policies and avoid penalties. Its key to maintaining trust and security in todays regulated environment.
CompTIA Security Plus: CompTIA Security+ is a great starting point for anyone entering cybersecurity. It covers the basics of managing threats, securing networks, and reducing risks. It's well-known worldwide and opens doors for beginners in IT security, providing a solid foundation for more advanced roles.
Cissp Certified Information Systems Security Professional: CISSP is designed for experienced professionals who want to dive deeper into cybersecurity management. It covers security strategies, risk management, and securing networks. Earning this certification shows you're ready for senior-level positions in cybersecurity, making you a top candidate for leadership roles.
Certified Ethical Hacker (CEH): CEH is perfect if you want to learn to think like a hacker and find vulnerabilities before the bad guys do. It focuses on ethical hacking, allowing you to find weaknesses in systems. With CEH, you can help organizations strengthen their security from the inside out.
Certified Information Security Manager: CISM is for people who manage company-wide security systems, focusing on aligning security with business goals. It's ideal for those in leadership positions overseeing large, complex security infrastructures. Getting CISM shows that you can lead security teams and ensure business continuity.
Cisa Certified Information Systems Auditor: CISA is all about auditing and assessing IT systems to ensure theyre secure and compliant with regulations. It's perfect for IT auditors and consultants who need to find and fix weaknesses in business systems. CISA shows you have the skills to protect companies from risks and legal issues.
Offensive Security Certified Professional (OSCP): OSCP is a hands-on certification that challenges you to think like a hacker in real-world situations. It's tough but rewarding, giving you the skills to test security systems and find vulnerabilities. If you're into penetration testing and offensive security, OSCP is a great way to prove your skills.
Certified Cloud Security Professional: CCSP focuses on securing cloud environments and protecting data stored in the cloud. It's ideal for IT professionals working with cloud technologies as cloud computing is rising rapidly. With the rise of cloud computing, this certification is becoming more valuable as companies rely on secure cloud infrastructures.
GIAC Security Essentials (GSEC): GSEC covers the essential cybersecurity skills needed to protect systems from threats, focusing on practical applications like network security and cryptography. It's a great certification for both technical and managerial roles, ensuring you can handle real-world cybersecurity challenges.
Cisco Certified CyberOps Associate: Cisco CyberOps Associate prepares you for working in a security operations center (SOC), covering everything from threat analysis to incident response. It's a great certification for those looking to specialize in security monitoring and protecting businesses from cyber threats.
Comptia Cysa+: CySA+ focuses on analyzing threats and responding to cyber-attacks using advanced monitoring and detection techniques. Its perfect for those working as security analysts in a SOC environment, helping organizations stay proactive against potential attacks.
CompTIA Cloud+ Certification: CompTIA Cloud+ certifies your ability to secure and manage cloud infrastructures. Its especially important in todays multi-cloud environments, where companies use different cloud providers. This certification ensures you have the skills to keep cloud systems running smoothly and securely.
Comptia Network+ N10 008: CompTIA Network+ provides foundational networking knowledge, covering everything from troubleshooting to network security. It's a great starting point for anyone interested in IT or cybersecurity. This certification proves you can build and maintain secure networks, which is essential for any business today.
CDPSE Certification: CDPSE focuses on data privacy and ensuring systems comply with global privacy laws. It's a must-have for professionals working on privacy solutions. With data privacy being a top concern for businesses, this certification proves you can help organizations protect sensitive information.
Cgrc Certification: CGRC certification focuses on managing risk and ensuring compliance with laws and regulations. It's perfect for professionals responsible for governance and compliance in their organizations. With CGRC, youll help businesses create risk management frameworks to avoid data breaches and fines.
Comptia Security Plus Certification: CompTIA Security+ covers the basics of cybersecurity, from network security to encryption. Its great for those new to the field, providing a strong foundation for building a career in IT security. This certification is recognized worldwide and is an ideal entry point for aspiring cybersecurity professionals.
Comptia A+ Core 1: CompTIA A+ Core 1 is all about the basics of IT support, including hardware, networking, and troubleshooting. Its a great starting point for anyone new to IT. With this certification, youll learn the essential skills needed to fix and support a wide range of tech issues in todays digital world.
Security Analyst: A Security Analyst is like a digital watchdog for a company. They constantly monitor networks to spot targeted dangers and vulnerabilities. When something suspicious happens, they jump into action, analyzing the situation and putting safety measures in place. Their hard work helps keep sensitive information safe and strengthens the organizations defenses against cyber threats.
Security Engineer: Security Engineers are the builders of safety measures in a company. They create and set up tools like firewalls and alarms to protect against cyber threats. If problems arise, they troubleshoot and find solutions. Their expertise is key in creating a secure space for everyone, making them essential for defending against online dangers.
Security Architect: Think of a Security Architect as a planner for digital security. They design strong security systems that fit the needs of the organization. By assessing potential risks and working closely with IT teams, they make sure that security is integrated into every part of the system. Their insights help protect companies from new cyber threats.
Incident Responder: Incident Responders are the heroes who tackle problems when a security breach happens. They act quickly to investigate what went wrong and minimize the damage. By analyzing alerts and coordinating recovery efforts, they help restore normal operations. Their ability to think on their feet is vital for strengthening defenses against future cyber incidents.
Penetration Tester: Penetration Testers, also known as ethical hackers, help keep organizations safe by testing their defenses. They pretend to be hackers to find weaknesses before real threats can exploit them. Using various tools, they provide valuable feedback on how to improve security. Their proactive approach ensures that companies are well-prepared for actual cyber challenges.
Forensic Analyst: Forensic Analysts are like detectives in the digital world. When a security incident occurs, they dig deep to figure out what happened and how. By analyzing evidence and recovering lost data, they help piece together the story. Their findings not only assist in solving cases but also improve security measures for the future.
Cybersecurity Consultant: Cybersecurity Consultants are friendly advisors who help organizations stay secure. They assess how safe a companys systems are and recommend ways to improve. By keeping up with the latest trends and threats, they offer customized solutions to enhance security. Their collaborative approach helps businesses navigate the complex world of cybersecurity with confidence.
Chief Information Security Officer (CISO): The Chief Information Security Officer (CISO) is the main leader for security in a company. They develop the overall security strategy and guide the team in protecting sensitive information. By aligning security goals with business objectives, they create a culture of awareness and preparedness. Their leadership is essential in keeping the organization safe from cyber threats.
Security Operations Center (SOC) Analyst: SOC Analysts are the frontline defenders against cyber dangers. They keep a close eye on security incidents in real-time, checking alerts and investigating anything suspicious. By working with other teams, they respond quickly to threats and minimize risks. Their dedication ensures that the organization remains strong and secure in a constantly changing environment.
Malware Analyst: Malware Analysts are like tech detectives who explore malicious software. They study malware samples to understand how they work and how to combat them. By creating detection methods and strategies, they help organizations stay safe from these threats. Their valuable insights enable companies to enhance security measures and effectively respond to future malware attacks.
By obtaining the Cyber Security Online Training in India after completing Cybersecurity online training, you will earn around 3.5 Lakh Per Annum, which is quite good for starters.
By enrolling in Cyber Security Online Course and gaining more experience in this field, your salary structure will eventually get better.
Your chances of getting into a well-established company will also increase.
After getting the Cyber Security Online Certificate Course, you will always receive a higher salary structure than normal employees.
Security Analyst
Security Engineer
Security Architect
Security Architect
Incident Responder
Penetration Tester
Forensic Analyst
Cybersecurity Consultant
Chief Information Security Officer (CISO)
Security Operations Center (SOC) Analyst
Malware Analyst
Obtaining this Cyber Security Online Certificate Course will help you to acquire the exact exposure to this field.
It will help you to grab a much higher salary package than other employees.
You will be able to work professionally as a Penetration Tester, Ethical Hacker, Cyber-Security Engineer, Security Analyst, etc.
Your chances of getting into a well-established company will also increase.
This Cyber Security Online Certificate Course will help you to sustain yourself in this direction in the long run.
By learning Cyber Security Online Training in India, your impression will reflect differently in front of the interviewer, and you might end up getting into a good workspace.
You will get an opportunity to work with government secret agencies.
You will come across various job opportunities.
In fact, you will get the chance to choose from a wide range of industries.
Working as a Security Analyst will indulge you in securing the overall information security of your company.
You will also have to assure internet security for individuals and organizations as well.
You will have to keep reviewing the data regularly.
Paying attention to minute details of the data will also be counted as your main job role.
The Emergence of Automotive Cybersecurity Threats
Harnessing the Power of Artificial Intelligence in Cybersecurity
Mobile Devices: A Growing Target for Cyber Attacks
Cloud Security Challenges and Solutions
Data Breaches: A Persistent Concern
IoT Security in the Era of 5G
Embracing Automation for Enhanced Cybersecurity
Targeted Ransomware Attacks
Escalating State-Sponsored Cyber Warfare
Mitigating Insider Threats Through Awareness
Addressing Cybersecurity Challenges in Remote Work Environments
Combating Social Engineering Attacks
Enhancing Security with Multi-Factor Authentication
Defending Against International State-Sponsored Attacks
Strengthening Identity and Access Management
Real-Time Data Monitoring for Early Threat Detection
Securing Connected Vehicles Against Cyber Threats
Leveraging AI for Enhanced Security
Ensuring Security for IoT Devices
Strengthening Cloud Security Measures
Heightened Regulatory Compliance- As data protection regulations are becoming stricter regularly, there is an increasing need for stronger cybersecurity measures.
Growing Adoption of Digital Technologies- There is widespread adoption of cloud computing, the Internet of Things (IoT), and big data. This has made cybersecurity a necessity. necessitates robust cybersecurity solutions.
Breter Managings, Pearson, Adobe, Zoylee, etc. are top-most companies hiring skilled Security Analysts.
Here, we will assist you to get into established organizations.
In fact, our team will consecutively help you in resume building, appearing in front of interviewers, and more.
Our trainers will also enhance your communication skills.
Our trainers will help you to pass the interview round.
Our trainers will prepare you to crack the interview procedure by conducting mock tests, and assignments as well.
You will also get a proper brief of other courses, and certifications respectively.
we train you to get hired.

By registering here, I agree to Croma Campus Terms & Conditions and Privacy Policy
+ More Lessons
Course Design By

Nasscom & Wipro
Course Offered By

Croma Campus

Stories
success
inspiration


career upgrad

career upgrad


career upgrad


career upgrad
05-Jul-2025*
07-Jul-2025*
02-Jul-2025*
05-Jul-2025*
07-Jul-2025*
02-Jul-2025*

You will get certificate after
completion of program

You will get certificate after
completion of program

You will get certificate after
completion of program
in Collaboration with






Empowering Learning Through Real Experiences and Innovation
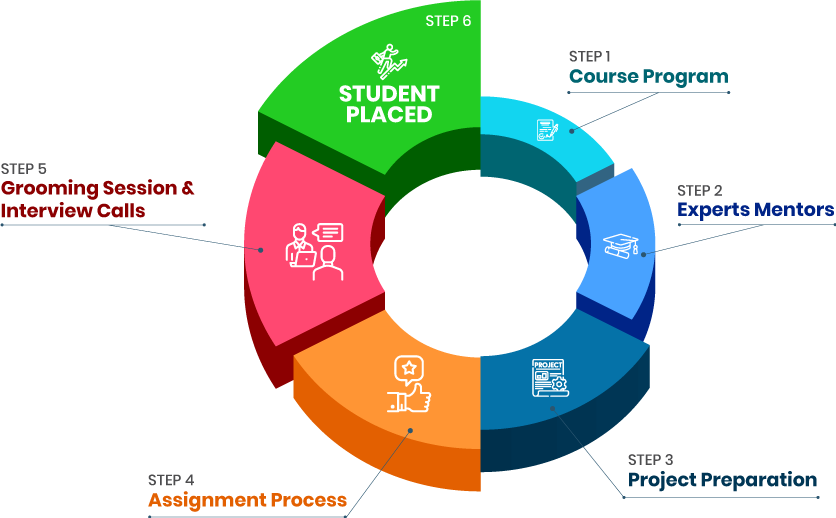
we train you to get hired.
Phone (For Voice Call):
+91-971 152 6942WhatsApp (For Call & Chat):
+91-971 152 6942Get a peek through the entire curriculum designed that ensures Placement Guidance
Course Design By


Course Offered By

Ready to streamline Your Process? Submit Your batch request today!
Cyber Security Online Training at Croma campus offers a unique vision into the world of hand-on practical Cyber Security Online Training. Croma campus is the Best Cyber Security Online Training Institute in India. Because The adviser handling Cyber Security Online training tips a trade experience of more than 10+ years. The view of becoming a freelancer growth harshly with the arsenal of Cyber Security Online in one’s portfolio. According to manifold reviews over the internet, we Ranked Best Cyber Security Online Training in India.
Croma campus is the Legend in offering placement to the students. Please visit our Placed Students List on our website. More than 2000+ students placed last year. It has a dedicated placement portal that caters to the needs of the students during placements. Croma campus conducts development sessions, including mock interviews, presentation skills to prepare students to face a challenging interview situation with ease. 100% placement record. 1000+ interviews organized.
Your course conclusion certificate will be auto made in the LMS once you see the below criteria
This Project will put you in an online corporate location. You will be coding a demo lending website. You will create & run code and have an opening to associate it with easy code created by our experts in real-time. The plan will last 7 days. You will be sent 1 email every 24 hours with your work provision for that day. It is totally FREE.
The ways to connect Croma Campus.

FOR QUERIES, FEEDBACK OR ASSISTANCE
Best of support with us
For Voice Call
+91-971 152 6942For Whatsapp Call & Chat
+91-9711526942