Course Design By
Nasscom & Wipro
Master Linux and Windows OS security (user permissions, patching, services)
Automate reconnaissance and exploitation task with Python and Bash script for
Web application security skills (SQLi, XSS, CSRF) and OWASP Top 10
Malware behavior skills and execute sandbox environments (e.g., Cuckoo Sandbox)
Cryptography skills: AES, RSA, SHA, HMAC, and implement secure PKI systems
Make use of SIEM tools and centralized log analysis with Splunk/ELK
Become incident response and digital forensics: timeline creation, memory analysis
Practice for CEH, OSCP, Security+, CISSP certification exams
SOC Analyst / Junior Security Analyst: 46LPA
Network Security Engineer: 68LPA
Pentester / VAPT Specialist: 710LPA
Incident Response / Forensics Trainee: 69LPA
Product Security / AppSec Positions: 812LPA
SOC or Junior Security Analyst (02 years): daily logs monitoring, alerts review, remediation level basic
Security Engineer / Network Defender (25 years): firewall administration, SIEM configuration, secure infrastructure
VAPT Specialist / Pentester (25 years): advanced-level testing, exploit chaining, web and network exploitation
Incident Responder / Forensics Specialist (5+ yrs): breach containment, malware memory analysis, legal evidence
Security Architect / Security Manager (510 yrs): enterprise security framework design, team lead
CISO / Director InfoSec (10+ yrs): strategy definition, governance, compliance, board-reporting
IT & Tech Ecosystem: Finance/fintech, MNCs such as Microsoft, Google, Cisco driving demand
Hands-on Labs: Hands-on tools, enterprise setup, and attack simulation zones to practice on
Expert Faculty: Trainers consist of IIT/NIT graduates, MNC security teams, ex-ethical hackers
Good Placements: Great connect-ness with Bangalore tech companies and start-ups, with extremely good placements
Digital Forensics Investigator: Examine disk images, memory dumps; retrieve deleted/hide data
Security Automation Engineer: Write scripts (Python/Bash) for automating scan, log examination, threat action
Security Consultant / AppSec Engineer: Do secure code review, threat modeling, compliance assessment
IT services,
fintech,
e-commerce,
telecommunication,
healthcare.
Course completion certificate with hands-on hours verified
CEH (Certified Ethical Hacker) preparation: ethical hacking, pentesting tool & technique
CompTIA Security+ preparation: security basics, network protection
OSCP preparation: advanced exploit writing & buffer overflow technique
Resume Workshop: Early lectures to create a strong Cyber Security resume
Weekly Mock Interviews: Regular frequency of frequent technical and HR mock interviews for confident preparation
Assessment Tests: Online aptitude, technical, and personality tests for familiarity with recruitment trends
Company-Specific Prep: Pre-visit classes to visiting companies to campus or via remote connections
Live Project Demonstration: Actual case studies (e.g., flag capture in CTF mode), pre-recruiter demo sessions
Placement Drives: Personal interview schedules, web and campus with partner firms
Provide Support: Salary negotiation, role matching, and official offer letters
Post-Placement Counseling: Relocation to your first workplace, with onboarding advice
Real-World Labs: Official full versions of Kali, Splunk, Metasploit, Burp, OWASP juice shop, Cuckoo sandbox
Sight Progress Monitoring: Lab and instructor scorecards on every project
Expert Teachers: IIT, ISB, former MNC cyber team trainers
Minimal Batch Size: 2025 students per class to give personal attention
Project-Oriented Syllabus: 4 major capstone projects:
Web-app pentesting with reporting
Network VAPT with scripting
Malware analysis and forensic dump
Incident response simulation
Round-the-Clock Support: 247 lab access, special doubt-clearing sessions
Certification Included: No additional fee for bundled CEH/Security+/OSCP prep
Robust Placement Support: Interview training, resume grooming, test prep, and offer negotiation assistance
OS fundamentals: filesystems, users, permissions
Networking: TCP/IP, ARP, DHCP, DNS, VLANs
Linux tools: bash scripting, cron jobs, user management
Windows tools: PowerShell, event viewer, UAC
Wireshark packet capture & analysis
Nmap host discovery, port scanning, OS detection
Firewall configuration: iptables, UFW, Windows Defender
IDS/IPS: Snort or Suricata installation
Reconnaissance: WHOIS, njRAT, Shodan
Web hacking: SQLi, XSS, CSRF, RCE exploitation
Tools: Metasploit, Burp Suite, OWASP ZAP
Reporting: risk assessment and documentation
Python: parsing files, sockets, requests
Bash: auto scanning, cron-run tasks
Construct small tools: vulnerability parser, port scanner
PE file analysis, run YARA, VirusTotal
Malware sandbox testing: Cuckoo
Encryption: RSA, ECC, AES
Hashing: SHA2 & 3; HMAC usage
PKI: CA/bare certificate management
Log aggregation: Splunk / ELK stack
Writing alerts, dashboards, threat detection
Incident detection drills
Incident classification & response playbooks
Disk imaging with dd, FTK / Autopsy forensic analysis
Memory dump analysis
Root cause and timeline reconstruction analysis
Choice between incident response, malware analysis, or pentesting
Final project presentation and report
Peer review and industry mentor feedback
we train you to get hired.
By registering here, I agree to Croma Campus Terms & Conditions and Privacy Policy
+ More Lessons
Course Design By
Nasscom & Wipro
Course Offered By
Croma Campus
Stories
success
inspiration
career upgrade
career upgrade
career upgrade
career upgrade
You will get certificate after
completion of program
You will get certificate after
completion of program
You will get certificate after
completion of program
in Collaboration with

Empowering Learning Through Real Experiences and Innovation
we train you to get hired.
Phone (For Voice Call):
+91-971 152 6942WhatsApp (For Call & Chat):
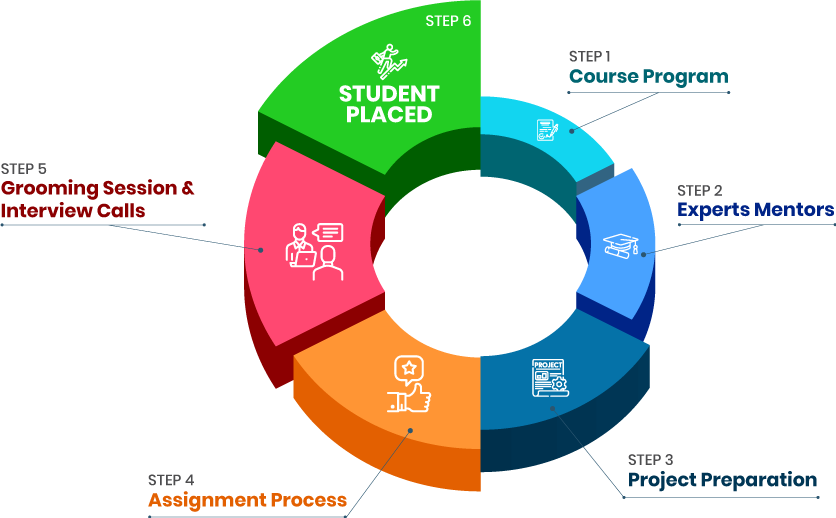
+91-971 152 6942Get a peek through the entire curriculum designed that ensures Placement Guidance
Course Design By
Course Offered By
Ready to streamline Your Process? Submit Your batch request today!
Not necessarily. We learn Bash and Python right from day one and automate step by step in the Cyber Security training in Bangalore. Technical skills are sufficient.
You will be practicing on virtual labs with Kali Linux, Cuckoo Sandbox, Splunk/ELK, and web-vulnerable app setups like OWASP Juice Shop.
Yes! You will be practicing mock tests every week and receiving feedback. We even have actual company-style tests.
Yes-you have homework to do from your instructor, one-on-one meetings, and 24×7 access to doubt sessions.
We have weekend batches and night batches with recordings so you will never miss classes.

Highest Salary Offered
Average Salary Hike
Placed in MNC’s
Year’s in Training

fast-tracked into managerial careers.
Get inspired by their progress in the
Career Growth Report.
FOR QUERIES, FEEDBACK OR ASSISTANCE
Best of support with us
For Voice Call
+91-971 152 6942For Whatsapp Call & Chat
+91-9711526942