Course Design By
Nasscom & Wipro
Understand how networks, operating systems, and web applications work
Master reconnaissance techniques and vulnerability scanning
Learn to perform penetration testing on real environments
Implement countermeasures to common attack techniques
Explore encryption, firewalls, and IDS/IPS systems
Understand compliance requirements and ethical laws in hacking
Ethical hackers fix problems before bad hackers attack. They find weak spots and help companies stay safe. They use skills to protect systems.
They act like puzzle solvers. They test systems in fun and smart ways. This work needs thinking, planning, and using cool tools.
The job is exciting and new every day. No two days are the same. You learn and solve different problems all the time.
Students learn with hands-on training. Training centers give practice labs. You try tools, break into test systems, and learn by doing real tasks.Certificates help students get good jobs.
After training, you earn certificates. These help you show skills and get jobs in top companies faster.
Security Analyst: Monitors network activity to detect threats and prevent intrusions
Cybersecurity Consultant: Provides guidance to organizations on how to build secure systems
Network Security Engineer: Maintains secure infrastructures for critical networks
Vulnerability Assessor: Conducts assessments to pinpoint system vulnerabilities
Incident Responder: Manages and investigates data breaches and cyber incidents
Performing security audits and assessments: Ethical hackers evaluate the safety of existing systems and recommend improvements
Penetration Testing: This means checking the system for weak points. Testers try things like fake login attacks. They also try sending tricky links. These tricks help find holes in the system.
Risk Analysis and Fixing: Look at what problems can happen. See which ones are big. Then try to fix them. This helps keep systems safe.
Finding and Stopping Problems: Watch for bad things like hackers. If something bad happens, find out how. Then fix it fast. This helps stop damage.
Write and Save Everything : Keep a record of all tests. Write what you found. Write how you fixed it. This helps others understand. It also shows the work was done.
IT & Software Services: Securing servers, networks, and SaaS platforms
Banking & Financial Services: Protecting transaction data and user credentials
Telecommunications: Ensuring secure voice and data transmission across networks
Healthcare: Securing patient records, insurance data, and regulatory compliance
E-commerce & Retail: Protecting payment gateways and customer information
Government Agencies: Managing digital surveillance and public safety platforms
Ethical Hacker Certificate: This certificate is known by many companies. It shows that you understand ethical hacking. It also proves you know how to test systems for safety. You learn how to find weak points.
Completion Certificate with Project Grading: This certificate highlights your practical work and project performance during the course.
Interview Readiness Certificate: Given to students who complete the grooming and interview readiness training, adding value during job applications.
Eligibility for Global Exams: Croma Campuss program prepares students to confidently sit for the EC-Council Certified Ethical Hacker (CEH) exam.
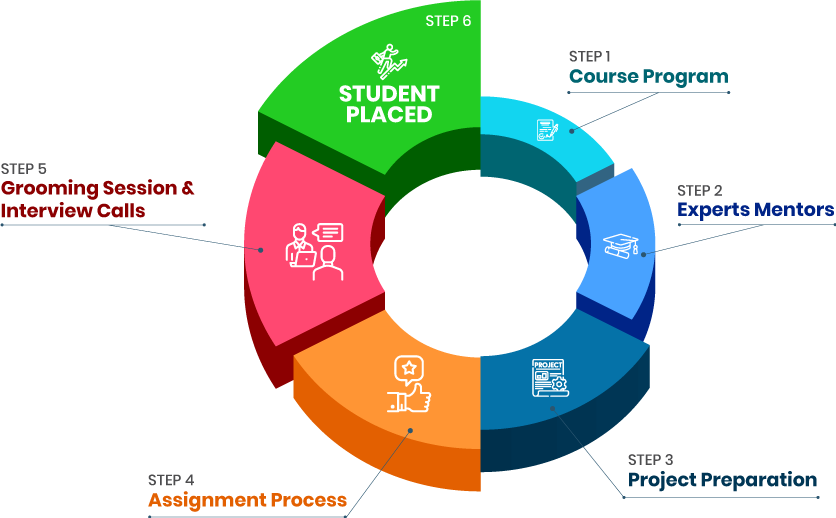
Expert Mentors: The teachers are experts. They have worked in cybersecurity for many years. They teach you what really happens in real jobs.
Live Projects: You do projects like real work. This helps you understand how to use what you learn.
Assignments and Tests: Every week, you get simple tasks. You also give small tests. This helps you remember things better.
Grooming Sessions : You learn soft skills. You learn to speak well. You learn to make a good resume. You give practice interviews.
Interview Help : This helps you get interviews and get placed.
we train you to get hired.
By registering here, I agree to Croma Campus Terms & Conditions and Privacy Policy
+ More Lessons
Course Design By
Nasscom & Wipro
Course Offered By
Croma Campus
Stories
success
inspiration
career upgrade
career upgrade
career upgrade
career upgrade
You will get certificate after
completion of program
You will get certificate after
completion of program
You will get certificate after
completion of program
in Collaboration with

Empowering Learning Through Real Experiences and Innovation
we train you to get hired.
Phone (For Voice Call):
+91-971 152 6942WhatsApp (For Call & Chat):
+91-971 152 6942Get a peek through the entire curriculum designed that ensures Placement Guidance
Course Design By
Course Offered By
Ready to streamline Your Process? Submit Your batch request today!
An ethical hacking course teaches how to test and protect computer systems. You learn how hackers break in and how to stop them. The course includes tools, methods, and safety steps. You can join an Ethical Hacking Course in Chennai to learn all these skills.
Anyone interested in cybersecurity can join. Students, IT professionals, and freshers are welcome. You just need basic computer knowledge. No coding is needed at the start. Many join to start a new career or improve their current job.
You will learn about network security, malware attacks, phishing, firewalls, and more. You also learn tools like Kali Linux, Metasploit, and Wireshark. A good Ethical Hacking Institute in Chennai will also help you understand real-world hacking problems.
The course is usually 2 to 4 months long. Some institutes offer fast-track or weekend classes. It depends on your schedule. You can ask the center to find the best option for your time.
Yes, you get a certificate after the course. It shows you have ethical hacking knowledge. It can help in job interviews. Some courses also prepare you for global certifications like CEH (Certified Ethical Hacker).
You can apply for jobs like ethical hacker, security analyst, or network security expert. Big IT companies, banks, and government sectors hire trained professionals. Ethical hacking Training in Chennai helps you get job-ready with real-time skills.
Yes, many institutes give job help. They share job openings, help with resumes, and conduct mock interviews. Some also connect you with companies directly. This support is useful for freshers and career switchers.

Highest Salary Offered
Average Salary Hike
Placed in MNC’s
Year’s in Training

fast-tracked into managerial careers.
Get inspired by their progress in the
Career Growth Report.
FOR QUERIES, FEEDBACK OR ASSISTANCE
Best of support with us
For Voice Call
+91-971 152 6942For Whatsapp Call & Chat
+91-9711526942