Course Design By
Nasscom & Wipro
Handling out different technology tools for maintaining relevancy.
To induce think like hacker aptitude in the students.
You can learn the concepts of the scan, defenses, and hacking networks without influencing real networks for identifying vulnerabilities.
Real-test environments for helping students to explore their acquired skills.
Ethical hackers must have a good grasp of multiple skillsets like Network stuffing, and SQL injection as well as others.
You can also showcase your skills with confidence.
You can also apply for a global certification exam with the right skill set.
Upon the completion of the course, you can be hired by top recruiters.
It helps out in safeguarding the assets of an organization from the attack of malicious hackers.
It is an amazing course that helps multi-nationals to manage their security at different levels.
You can manage customer relationships and overall customer services by storing and securing customer data.
It increases overall ROI and sales/marketing team efforts as well as updating business information.
Researching out the organizational data structures.
Conducting the multiple penetration tests.
Identifying & implementing our security laws throughout the process.
Able to properly identify the hidden vulnerabilities of the system.
Identifying the areas of high-level security.
we train you to get hired.
By registering here, I agree to Croma Campus Terms & Conditions and Privacy Policy
+ More Lessons
Course Design By

Nasscom & Wipro
Course Offered By

Croma Campus

Stories
success
inspiration


career upgrad

career upgrad


career upgrad


career upgrad
19-Jul-2025*
21-Jul-2025*
23-Jul-2025*
19-Jul-2025*
21-Jul-2025*
23-Jul-2025*

You will get certificate after
completion of program

You will get certificate after
completion of program

You will get certificate after
completion of program
in Collaboration with






Empowering Learning Through Real Experiences and Innovation
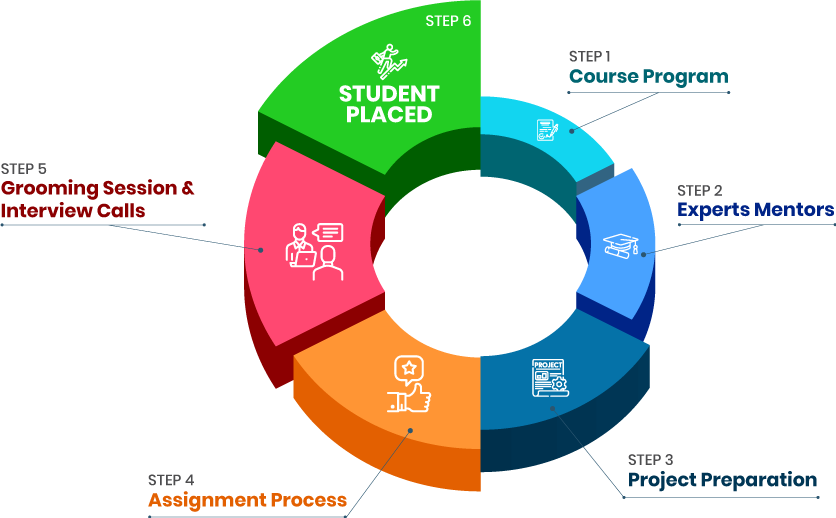
we train you to get hired.

Phone (For Voice Call):
+91-971 152 6942WhatsApp (For Call & Chat):
+91-971 152 6942Get a peek through the entire curriculum designed that ensures Placement Guidance
Course Design By


Course Offered By

Ready to streamline Your Process? Submit Your batch request today!
Certain basic limitations must get considered by Ethical Hackers before proceeding with their proceedings.
Yes, Ethical Hacking needs some aspects of coding like Python, SQL, C++ as well as Ruby.
Ethical Hacking doesn’t require coding but it is difficult to proceed with complicated processes without coding.
It is important to learn programming to become a good hacker.
Ethical Hacking is booming due to the continuous involvement of IT processes at the organizational level.
Croma Campus provides Best Ethical Hacking Training in Noida as per the current industry standards. Our training programs will enable professionals to secure placements in MNCs.
Our strong associations with top organizations like HCL, Wipro, Dell, Birlasoft, TechMahindra, TCS, IBM, etc. makes us capable to place our students in top MNCs across the globe.
We provide video recording tutorials of the training sessions, so in case if the candidate missed any class, he/she can utilize those video tutorials. All our training programs are based on live industry projects. Live Project based training with trainers having 5 to 15 years of Industry Experience.
We provide free demo classes in form of online and offline classes that are tailored to provide a complete overview of the course before joining the training. These are guided by expert ethical Hackers and explain the importance of the Ethical hacking training institute in Noida.

FOR QUERIES, FEEDBACK OR ASSISTANCE
Best of support with us
For Voice Call
+91-971 152 6942For Whatsapp Call & Chat
+91-9711526942