Course Design By
Nasscom & Wipro
The course helps to increase the overall productivity of engineers.
It helps to save overall time and energy that can be used for other things.
MCSE certification course helps to gain the necessary skills.
You get the opportunity to participate in Microsoft events, conferences, training sessions and more.
You learn to work on Microsoft tools and optimizing existing Microsoft solutions.
You will learn to deploy new Microsoft solutions in the company.
You can work on Windows server, exchange servers, SQL servers and more.
The skilled MCSE certified professional may earn up to USD 96,125 per annum and even higher at the fresher level.
The network administrator can earn an average salary of USD 50, 268 per annum.
In India, the fresher can earn around 3-4 lac per annum.
You can apply for the global certification exam.
Make your profile stand out from the crowd.
Get prepared for leading industries and get hired by top brands at a high salary.
Why MCSE
Why choose MCSE as a career option
You must have ability to solve complicated problems in multi-platform environment.
Excellent verbal and written communication
You must have ability to lead technical teams
Must have good organizational and management skills.
You must be able to explain concepts and communicate with system administrator, and MIS managers.
You get the chance to work with leading industries and earn well.
You can improve your communication skills and innovative skills.
Prepare yourself for leading industries.
Establish yourself as a knowledgeable resource demanded by industries.
The certificate helps to operate on Microsoft windows and improved the overall productivity of system engineers.
You will get the training certificate after the completion of the course.
The skills during your interview will get improved.
we train you to get hired.

By registering here, I agree to Croma Campus Terms & Conditions and Privacy Policy
Course Design By

Nasscom & Wipro
Course Offered By

Croma Campus

Stories
success
inspiration


career upgrad

career upgrad


career upgrad


career upgrad
12-Jul-2025*
07-Jul-2025*
09-Jul-2025*
12-Jul-2025*
07-Jul-2025*
09-Jul-2025*

You will get certificate after
completion of program

You will get certificate after
completion of program

You will get certificate after
completion of program
in Collaboration with






Empowering Learning Through Real Experiences and Innovation
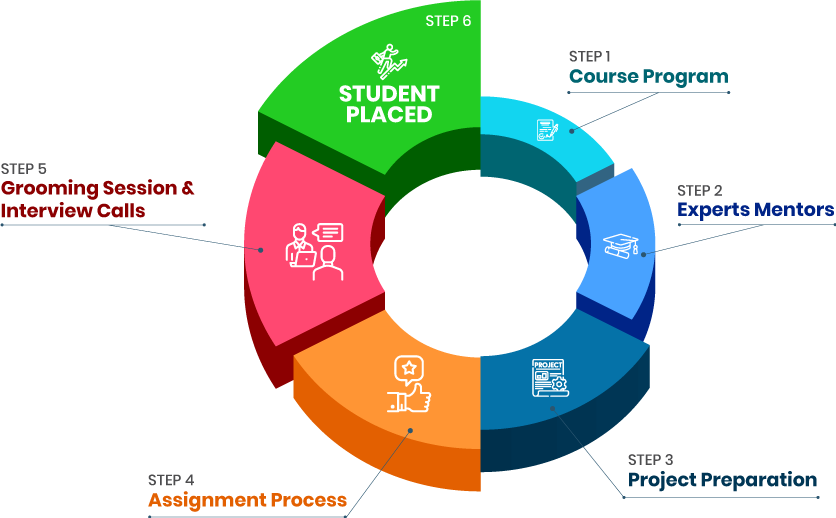
we train you to get hired.
Phone (For Voice Call):
+91-971 152 6942WhatsApp (For Call & Chat):
+91-971 152 6942Get a peek through the entire curriculum designed that ensures Placement Guidance
Course Design By


Course Offered By

Ready to streamline Your Process? Submit Your batch request today!
No, there is no need to have previous experience. You are not required to be from an IT background even.
Yes, all the training modules are updated as per the international standards and requirements.
It is widely used by various industries. Many hiring managers look for professionals who can work on Microsoft tools for optimizing existing Microsoft solutions. Also, they look for certified professionals that can administer new solutions to systems.
You must have a basic knowledge of operating computers. A person who is not from an IT background can also do the course.

FOR QUERIES, FEEDBACK OR ASSISTANCE
Best of support with us
For Voice Call
+91-971 152 6942For Whatsapp Call & Chat
+91-9711526942